Category: Cybersecurity
-
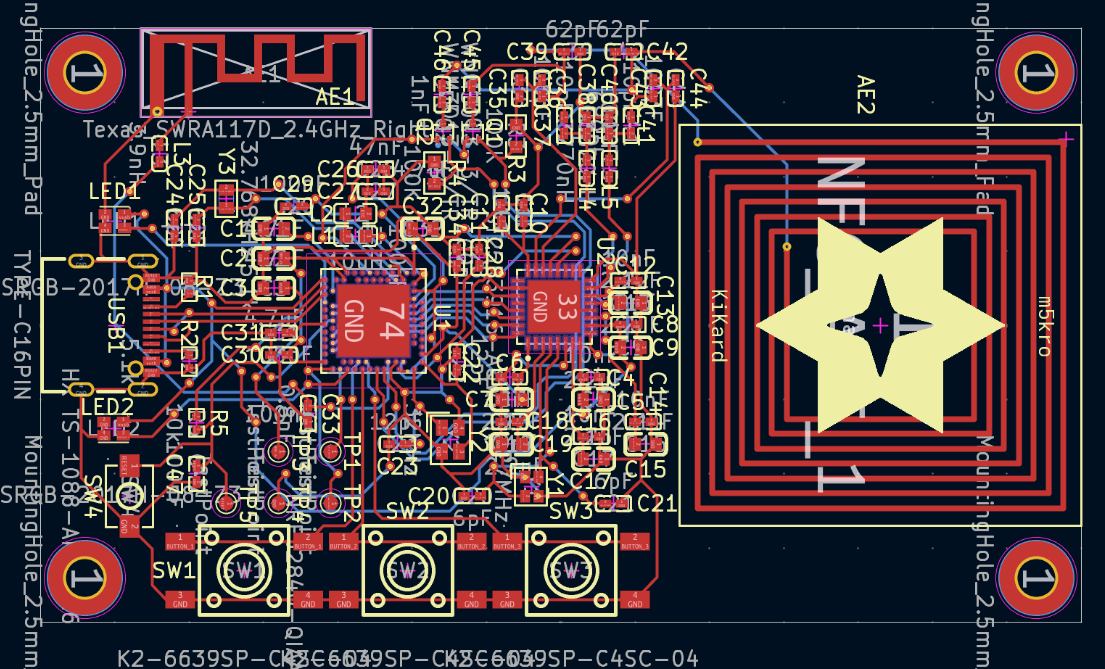
Challenges of Designing Hardware
A few months ago, I set out to create KiKard, a custom NFC testing board meant for part two of my NFC Card emulation series. It was an ambitious project with some pretty lofty goals, but I felt somewhat confident that I could complete it within a month. Unfortunately, things did not go according to…
-

VMs VS Baremetal in Cybersecurity
Virtual machines (VMs) have been around for a long time. Many people use them daily for various tasks, but let’s focus on VMs for offensive and defensive cybersecurity. Offensive Virtual Machines Pros: Quickly spin up premade images Supports most OS’s Little to no risk of corrupting the host system Cons: May be slow due to…
-

Bluetooth LE Encryption
A few days ago, I stumbled upon BLEUnlock, a project that used BLE (Bluetooth Low Energy) to unlock Mac devices based on the proximity of a secondary device, like an iPhone or Apple Watch. After roughly looking through the repository, it became apparent that the software lacked encrypted communications to facilitate authentication. Instead, it merely…
