Kro’s Nest
Home of m5kro
Latest Posts
-

AI Terminal Automation
Over a year ago, I released Terminal Commander, a tool that used LLMs to perform terminal operations. But the tool was very rudimentary, lacking in true interactive control over the command line. Since then, I’ve redesigned the entire system, allowing automation from the AI with little to no human intervention. Let’s take a look at…
-
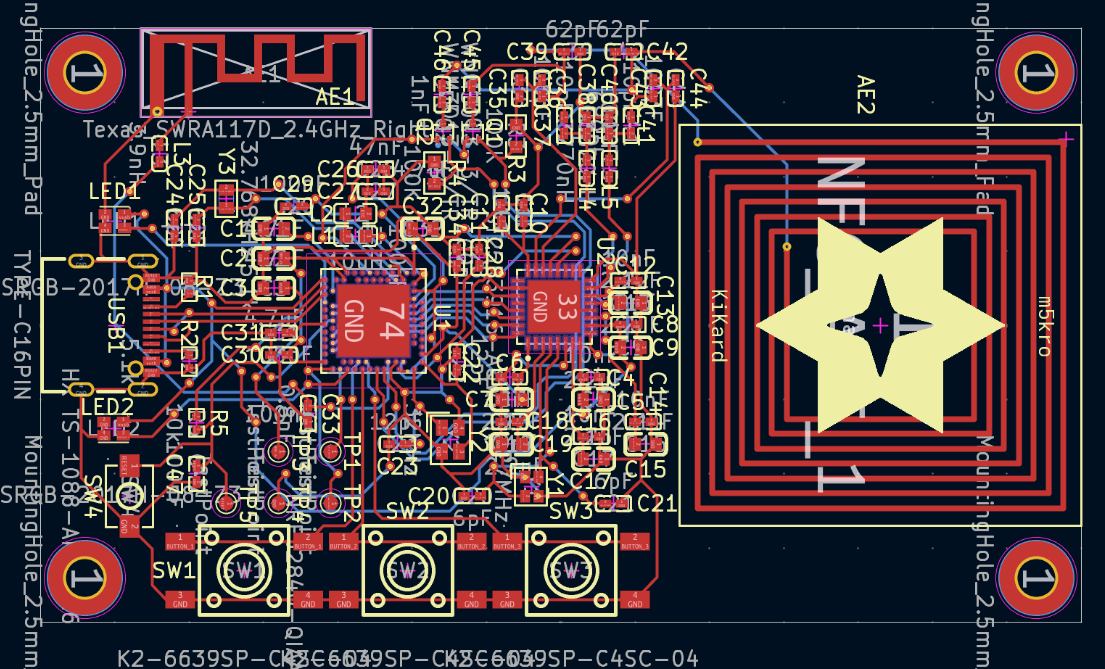
Challenges of Designing Hardware
A few months ago, I set out to create KiKard, a custom NFC testing board meant for part two of my NFC Card emulation series. It was an ambitious project with some pretty lofty goals, but I felt somewhat confident that I could complete it within a month. Unfortunately, things did not go according to…
-

VMs VS Baremetal in Cybersecurity
Virtual machines (VMs) have been around for a long time. Many people use them daily for various tasks, but let’s focus on VMs for offensive and defensive cybersecurity. Offensive Virtual Machines Pros: Quickly spin up premade images Supports most OS’s Little to no risk of corrupting the host system Cons: May be slow due to…
