Ever wonder what information websites get from your browser? At first glance, you might think it’s just basic stuff, like a return address, but it’s much more complicated than it seems. In this article, we’ll go over what sites can see about your device and why they would need this data.
Note: You can check out all the things mentioned here at https://github.com/m5kro/browser-test
Headers
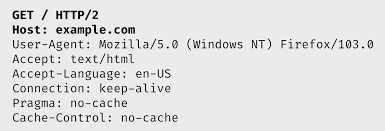
Let’s start with some common headers. When you send a request to a website, your computer sends a user agent string, the URI of the URL, any cookies you have, and a few other parameters. The user agent string contains what OS you use and your browser version. This may sound concerning but most sites use this to determine if they should serve you the mobile or desktop page. Some other notable headers are language support and what types of data your browser accepts.
Javascript

Javascript lets websites probe for specific information about your device. The biggest concern is the ability to load third party cookies. This essentially lets big companies like Google or Amazon track what websites you visit or what products you’re interested in. Most ad blockers or privacy extensions block third party cookies from loading, but if you’re using Chrome, Google can still see everything you do. Other, slightly less concerning things include, mouse tracking, window focus tracking, and devtools (inspect element) detection.
WebRTC

WebRTC, or Web Real-Time Communications, is a protocol that allows browsers to create peer to peer connections with other browsers. This is useful for things like real time voice, video, or texting as it reduces the latency caused by intermediary servers. However, due to how the protocol works, it can sometimes perform what’s called a “WebRTC Leak”.
To discover each other, browsers first need to send their public IP addresses to a middleman, known as a STUN server, and this becomes a problem when the user is using a VPN. Some VPNs, around 20%, don’t drop connections going through unprotected channels, causing things like WebRTC to “leak” the user’s real IP address.
If you can’t tell already, this is a major privacy concern as it exposes sensitive information to the web server. This problem can be further exacerbated by IP geolocation, which we will talk about next.
IP Geolocation

Like geo guesser but with IP addresses instead of google maps, IP geolocation figures out where a connection originates from. This is done through huge tables that map each IP address to a location as accurate as the city of where the IP is located. There are companies specialized in creating and hosting these tables and where they get this information is still a mystery.
Conclusion
Your browser is not your friend when it comes to privacy. Plenty of identifying information is freely released to any website you visit. There are certainly ways to combat this, such as disabling javascript, but they come at the cost of core features. It’s really up to you how much of your life you want to give away.

